
Secret Recipe
Platform : TryHackMe
Type : Challenge (Forensic)
Difficulty : ⭐⭐⭐☆☆
Table of contents
Introduction
Jasmine owns a famous New York coffee shop Coffely which is famous city-wide for its unique taste. Only Jasmine keeps the original copy of the recipe, and she only keeps it on her work laptop. Last week, James from the IT department was consulted to fix Jasmine’s laptop. But it is suspected he may have copied the secret recipes from Jasmine’s machine and is keeping them on his machine.Image showing a Laptop with a magnifying glass.
His machine has been confiscated and examined, but no traces could be found. The security department has pulled some important registry artifacts from his device and has tasked you to examine these artifacts and determine the presence of secret files on his machine.
Questions
Question 1
How many files are available in the Artifacts folder on the Desktop ?
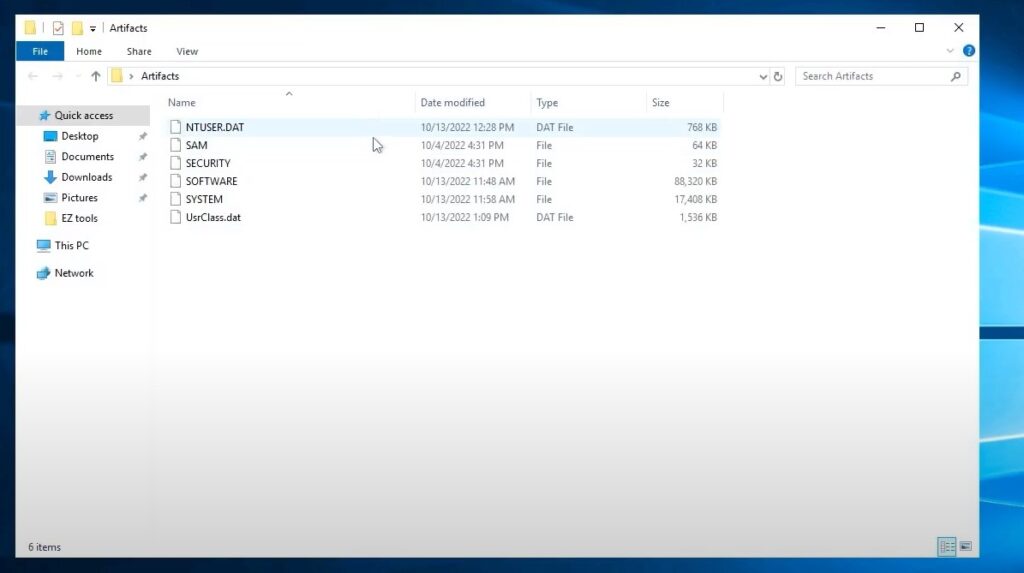
Answer : 6
Question 2
What is the Computer Name of the Machine found in the registry ?
We can find the answer in the SYSTEM\ControlSet001\Control\ComputerName\ComputerName registry key :
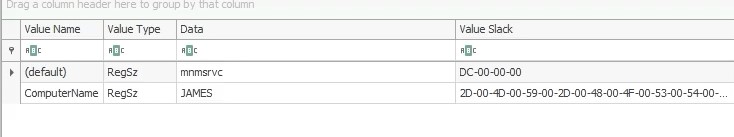
Answer : JAMES
Question 3
When was the Administrator account created on this machine ? (Format: yyyy-mm-dd hh:mm:ss)
We can find the answer in the SAM\SAM\Domains\Account\Users registry key :
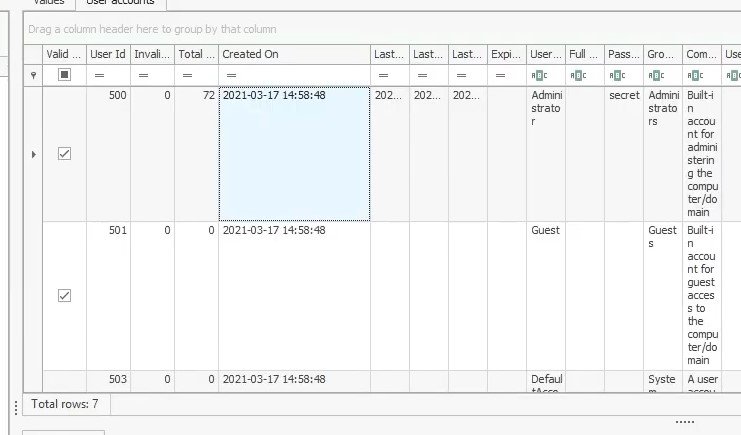
Answer : 2021-03-17 14:58:48
Question 4
What is the RID associated with the Administrator account ?
The users RIDs can be found in the SAM\SAM\Domains\Account\Users registry key :
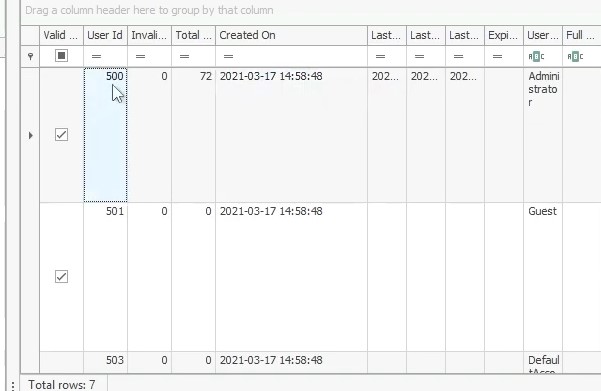
Answer : 500
Question 5
How many User accounts were observed on this machine ?
In the SAM\SAM\Domains\Account\Users\Names registry key, we can find users who logged in on the system :
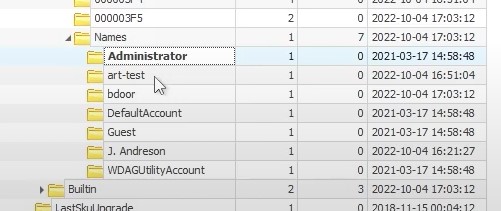
Answer : 7
Question 6
There seems to be a suspicious account created as a backdoor with RID 1013. What is the Account Name ?
Like for question 4, we can find a list of users RIDs and their corresponding account name in the SAM\SAM\Domains\Account\Users
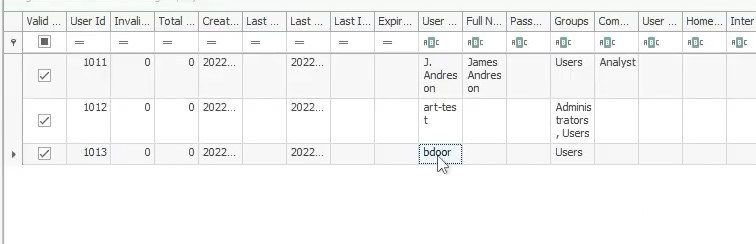
Answer : bdoor
Question 7
What is the VPN connection this host connected to ?
Answer in SYSTEM\ControlSet001\Services\bam\State\UserSettings\S-1-5-21-1966530601-318510712-10604624-500 :
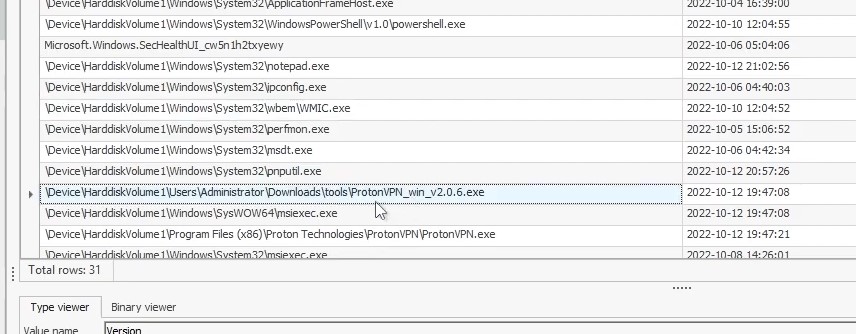
Answer : ProtonVPN
Question 8
When was the first VPN connection observed ? (Format: YYYY-MM-DD HH:MM:SS)
We can find a list of networks in the SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList registry key :
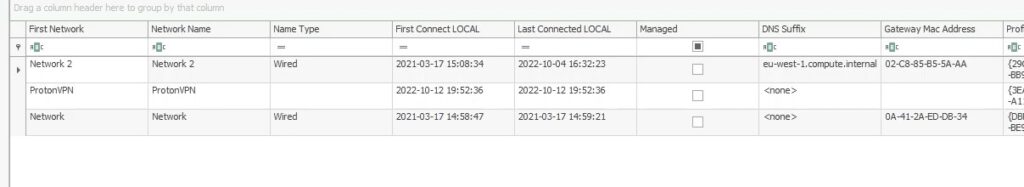
Answer : 2022-10-12 19:52:36
Question 9
There were three shared folders observed on his machine. What is the path of the third share ?
In the SYSTEM\ControlSet001\Services\LanmanServer\Shares registry key, we can find a list of SMB shares :
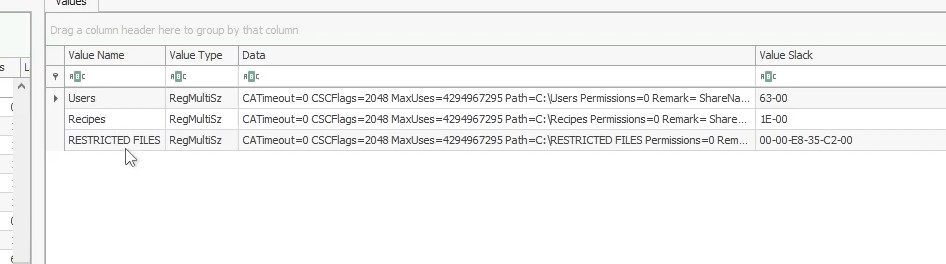
Answer : C:\RESTRICTED FILES
Question 10
What is the last DHCP IP assigned to this host ?
Information regarding network interfaces can be found in SYSTEM\ControlSet002\Services\Tcpip\Interfaces registry key :
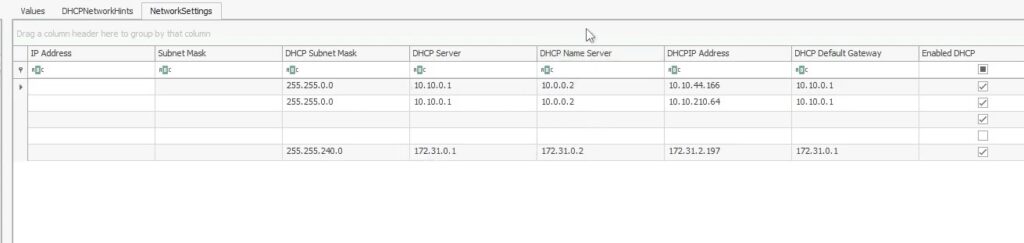
Answer : 172.31.2.197
Question 11
The suspect seems to have accessed a file containing the secret coffee recipe. What is the name of the file ?
On Windows, when you access a file, it is saved in a history of recent files in the explorer. We can find this history in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\pdf registry key :
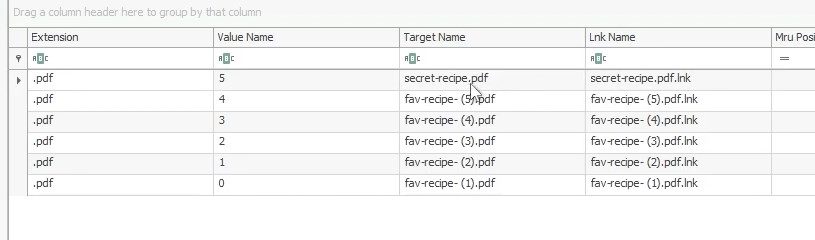
Answer : secret-recipe.pdf
Question 12
The suspect ran multiple commands in the run window. What command was run to enumerate the network interfaces ?
On Windows, the run window can be opened by pressing WIN + R. In this window, you can directly run a Windows command. An history of those commands can be found in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU :
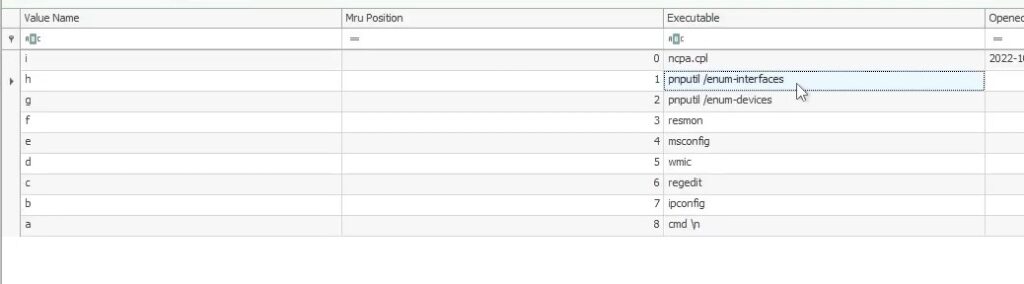
Answer : pnputil /enum-interfaces
Question 13
In the file explorer, the user searched for a network utility to transfer files. What is the name of that tool ?
When searching for something in the file explorer on Windows, your query is stored in an history. It can be found in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQuery registry key :
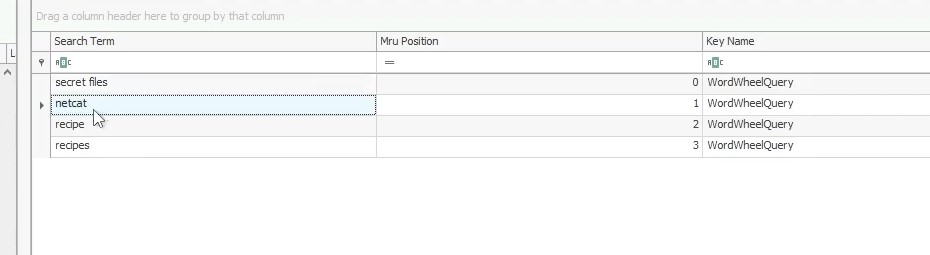
Answer : netcat
Question 14
What is the recent text file opened by the suspect ?
As for question 11, we can find recently accessed files in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs registry key :
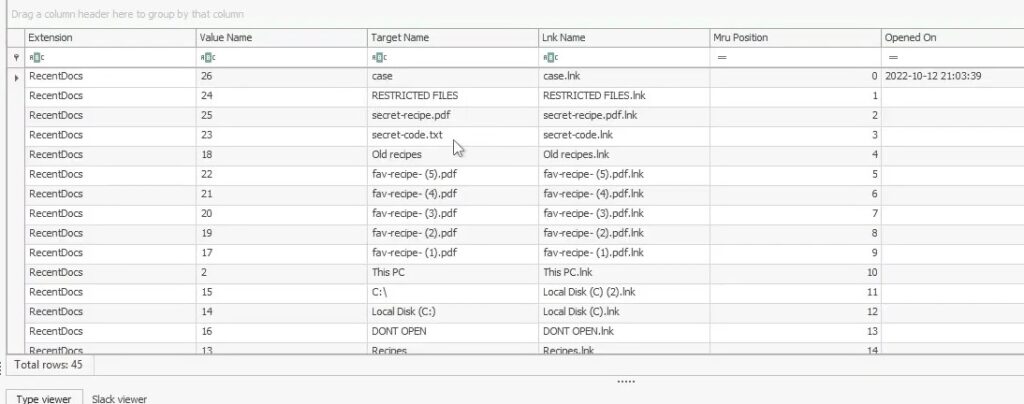
Answer : secret-code.txt
Question 15
How many times was Powershell executed on this host ?
On Windows, the number of times you run a program is stored in the registry. We can find this information in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count registry key :
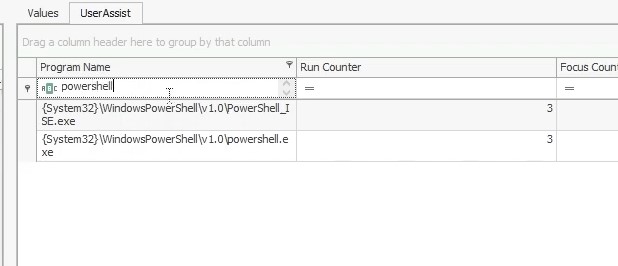
Answer : 3
Question 16
The suspect also executed a network monitoring tool. What is the name of the tool ?
Answer in SYSTEM\ControlSet001\Sercices\bam\State\UserSettings\S-1-5-21-1966530601-3185510712-10604624-500 :
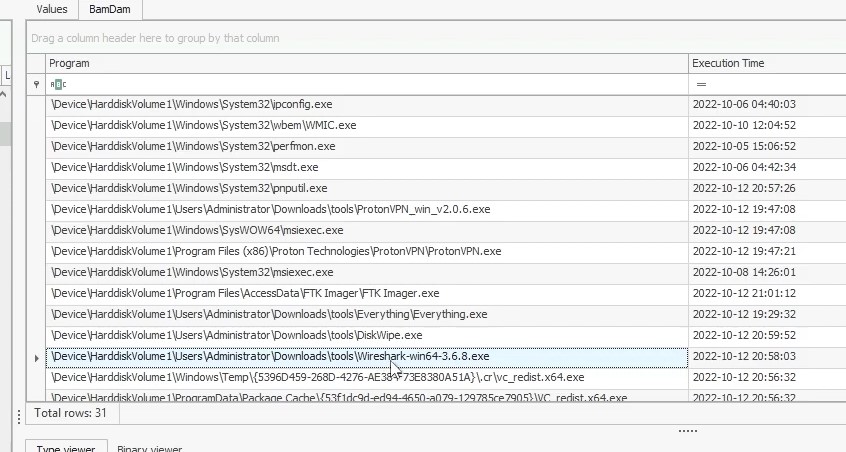
Answer : wireshark
Question 17
Registry Hives also notes the amount of time a process is in focus. Examine the Hives. For how many seconds was ProtonVPN executed ?
Answer in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count :
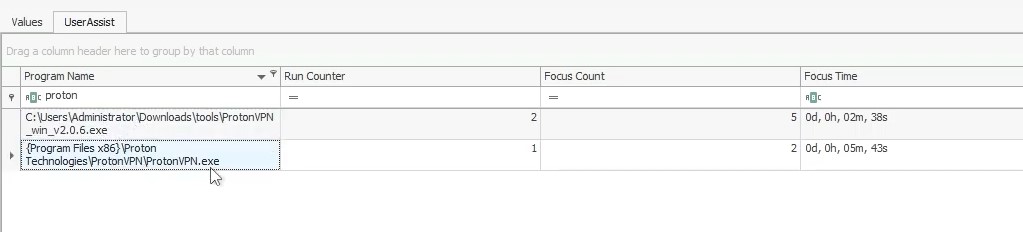
Answer : 343 (5 minutes x 60 + 43)
Question 18
Everything.exe is a utility used to search for files in a Windows machine. What is the full path from which everything.exe was executed ?
As for question 15, we can find the answer in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count registry key :
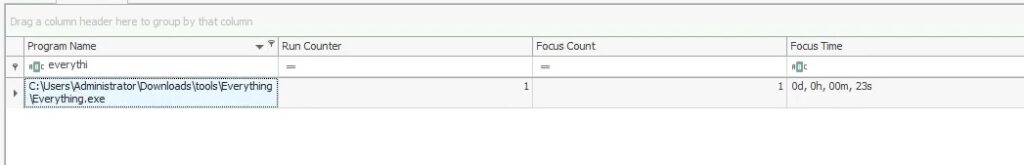
Answer : C:\Users\Administrator\Downloads\tools\Everything\Everything.exe